Teaching
Things I think people should know.
Ideas like least privilege, defence in depth, and zero trust in cybersecurity are commonly called principles or concepts. These principles guide the development, implementation, and management of secure systems. They serve as foundational elements that inform best practices and strategies in cybersecurity. Each principle addresses specific security and risk management aspects, aiming to reduce vulnerabilities and protect against threats.
Least Privilege
This principle dictates that users, systems, and programs should have only the minimum levels of access—or permissions—necessary to perform their tasks. The goal is to limit the potential damage from accidents, errors, or unauthorized use.
Defense in Depth
This concept involves using multiple layers of security controls and measures spread throughout an information system. If one layer fails, others will continue to provide protection, making it harder for an attacker to breach the entire system.
Zero Trust
Zero trust is a security model that assumes no entity inside or outside the network is trusted by default. Verification is required from everyone trying to access resources in the network, regardless of their location or whether they are inside the network perimeter. This approach minimizes the risk of unauthorized access and lateral movement within the network.
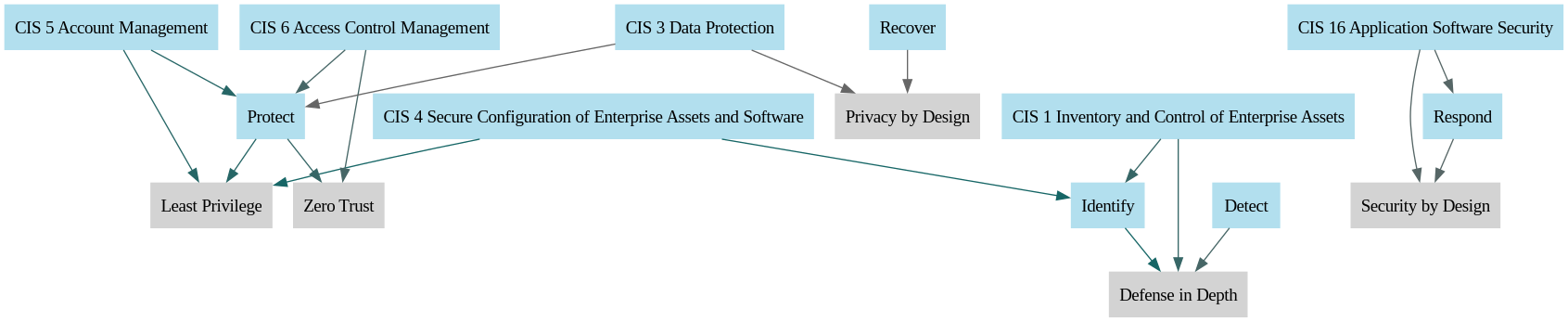
The Center for Internet Security Critical Security Controls (CIS Controls) is a set of best practices designed to help organizations prevent, detect, and respond to cyber threats. These controls are broadly applicable and foundational to cybersecurity efforts in various organizations. Mapping the concepts of least privilege, defence in depth, zero trust, security by design, and privacy by design to the CIS Controls can highlight how these principles underpin and are integral to implementing the controls.
Least Privilege
Control 4: Secure Configuration of Enterprise Assets and Software: Ensuring systems are configured with only the necessary permissions aligns with the principle of least privilege.
Control 5: Account Management: Directly relates to managing the creation, use, and deletion of system and application accounts to ensure users have only the access they need to perform their roles.
Defense in Depth
Control 1: Inventory and Control of Enterprise Assets: Knowing what assets you have is the first layer of defence.
Control 9: Malware Defenses: Implementing multiple layers of malware defences ensures that if one layer fails, others will provide protection.
Control 12: Network Infrastructure Management: Involves multiple layers of network controls and segmentation to protect against lateral movement.
Control 18: Penetration Testing: Testing multiple layers of defences to identify weaknesses.
Zero Trust
Control 11: Network Monitoring and Defense: Monitoring network traffic ensures that only legitimate traffic is allowed, aligning with the zero trust principle of not trusting any entity by default.
Control 5: Account Management: Enforcing principles of least privilege and access control in line with zero trust.
Control 16: Application Software Security: Ensuring applications enforce access controls and authentication in a manner consistent with zero trust principles.
Security by Design
Control 3: Data Protection: Incorporating security controls to protect data at rest, in transit, and during processing.
Control 16: Application Software Security: Involves securing applications from the development phase through deployment and maintenance.
Control 18: Penetration Testing: Testing security early and often is part of security by design.
Privacy by Design
Control 3: Data Protection: Protecting data privacy by ensuring that personal data is encrypted, anonymized, or otherwise protected.
Control 14: Security Awareness and Skills Training: Training developers and system administrators on incorporating privacy into their designs and practices.
import pandas as pd
from graphviz import Digraph
csv_paths = {
'CIS2Concepts': 'CIS2Concepts.csv',
'CIS2NIST': 'CIS2NIST.csv',
'NIST2Concept': 'NIST2Concept.csv'
}
csv_dataframes = {}
for key, path in csv_paths.items():
csv_dataframes[key] = pd.read_csv(path)
csv_structures = {key: df.head() for key, df in csv_dataframes.items()}
csv_structures
def generate_edges(data, source_col, target_col):
edges = []
for _, row in data.iterrows():
source = row[source_col]
target = row[target_col]
edges.append((source, target))
return edges
edges_CIS2Concepts = generate_edges(csv_dataframes['CIS2Concepts'], 'CIS Control', 'Concept')
edges_CIS2NIST = generate_edges(csv_dataframes['CIS2NIST'], 'CIS Control', 'NIST CSF Function')
edges_NIST2Concept = generate_edges(csv_dataframes['NIST2Concept'], 'NIST CSF Function', 'Concept')
combined_edges = edges_CIS2Concepts + edges_CIS2NIST + edges_NIST2Concept
dot = Digraph(comment='Cyber Security Concepts Mapping', format='png')
dot.attr('node', shape='box', style='filled')
for i, edge in enumerate(combined_edges):
dot.node(edge[0], color='lightblue2')
dot.node(edge[1], color='lightgrey')
dot.edge(edge[0], edge[1], color=f'#{i % 6 + 1}66666')
output_graph_path = 'CyberSec_Concepts_Mapping'
dot.render(output_graph_path)